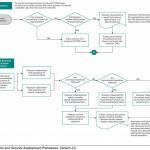
Network Segmentation
The use of network segmentation can reduce the scope and complexity of PCI compliance.
Video on using Palo Alto Networks for network segmentation and policy-based control over applications, users, and content - resulting in lower cost and complexity of PCI audits.
Scope of Assessment – Network Segmentation
- Network segmentation isolates systems that store, process, or transmit cardholder data from those that do not
- Not a PCI DSS requirement, but can reduce scope, cost, risk
- Without network segmentation, the entire “flat” network is in scope for PCI DSS
- Documenting cardholder data flows aids understanding and effective network segmentation
- No “cook book” approach to network segmentation
Click here to view the white paper titled, ‘PacketSentry Virtual Segmentation a Practical Approach to PCI Network Segmentation and Scope Reduction.’
A properly segmented network starts with three type of controls:
- Preventative controls
- Detective controls
- Corrective controls
Preventative network controls are going to be firewall rules and VLAN ACLs and any other controls that prevent or control access. Detective network controls are going to be related to the monitoring you implement. Monitoring can be real time and/or log analysis after the fact, but it should not be limited to just access to/from the CDE. Monitoring also needs to include monitoring the network traffic for anomalous traffic. Finally, you need corrective controls to ensure that any issues discovered with the preventative and detective controls are addressed as soon as possible. Corrective controls are usually generated as action items created from such things as the lessons learned from an incident response plan or findings from an audit.
Preventative Controls
The following would be considered the minimum preventative controls when talking about network segmentation.
- Firewall(s) with rules that restrict traffic to a limited number of ports to/from the cardholder data environment.
- Router(s) with ACLs that restrict traffic to a limited number of ports to/from the cardholder data environment.
- VLAN(s) with ACLs that restrict traffic to a limited number of ports to/from the cardholder data environment.
- Private wireless network(s) use a separate VLAN(s) from the cardholder data environment with access controls enforced for any access to the cardholder data environment from wireless. Private wireless access points are configured with WPA2 using Enterprise authentication and AES 128-bit or greater encryption.
- Software firewall on server(s) in the cardholder data environment that restricts traffic to a limited number of ports/services to/from the server(s).
- Restricted administrative access to infrastructure devices in or controlling access to the cardholder data environment.
- Access controls that restrict administrative and end-user access to applications in the cardholder data environment or that access the cardholder data environment.
Detective Controls
The following would be considered the minimum detective controls when talking about network segmentation.
- Network and host intrusion detection/prevention systems that monitors the aforementioned firewalls, routers, VLANs and servers that are protecting the cardholder data environment and generate alerts to appropriate personnel when an intrusion or incident is detected.
- Daily analysis of infrastructure device configurations to ensure that only approved configuration changes are made to these devices.
- Daily monitoring of devices to alert on any foreign devices that are added or when devices are removed from the network.
- Daily analysis of log data from the preventative controls to find potentially anomalous log entries that indicate a variance in the preventative controls or a potential incident.
- Change management records for all infrastructure devices, servers and applications in-scope for PCI compliance.
Corrective Controls
The following would be considered the minimum corrective controls when talking about network segmentation.
- Change management procedures.
- Incident response plan(s) for addressing any issues identified by the detective controls.
- Root Cause Analysis (RCA) procedures.
- Action plans that result from the incident response process that require changes to the preventative and/or detective controls. At a minimum, the action plans must document the correction needed, the person(s) responsible for getting the correction completed and the timeframe for the correction to occur.
- Internal audit review of the preventative and detective controls.
- QSA review of the preventative and detective controls.