Cyber Tools
Tools
- Familytreenow
- Meterpreter - Whenever posible use this. Use this behind a tunel like ngrok so the exploit does not connect back to your local host directly
- msfconole
- use exploit/multi/misc/java_rmi_server
- set RHOST
- set payload
- exploit
- sessions -l
- sessions -i l
- haveibeenpwned - has an email address been compromised
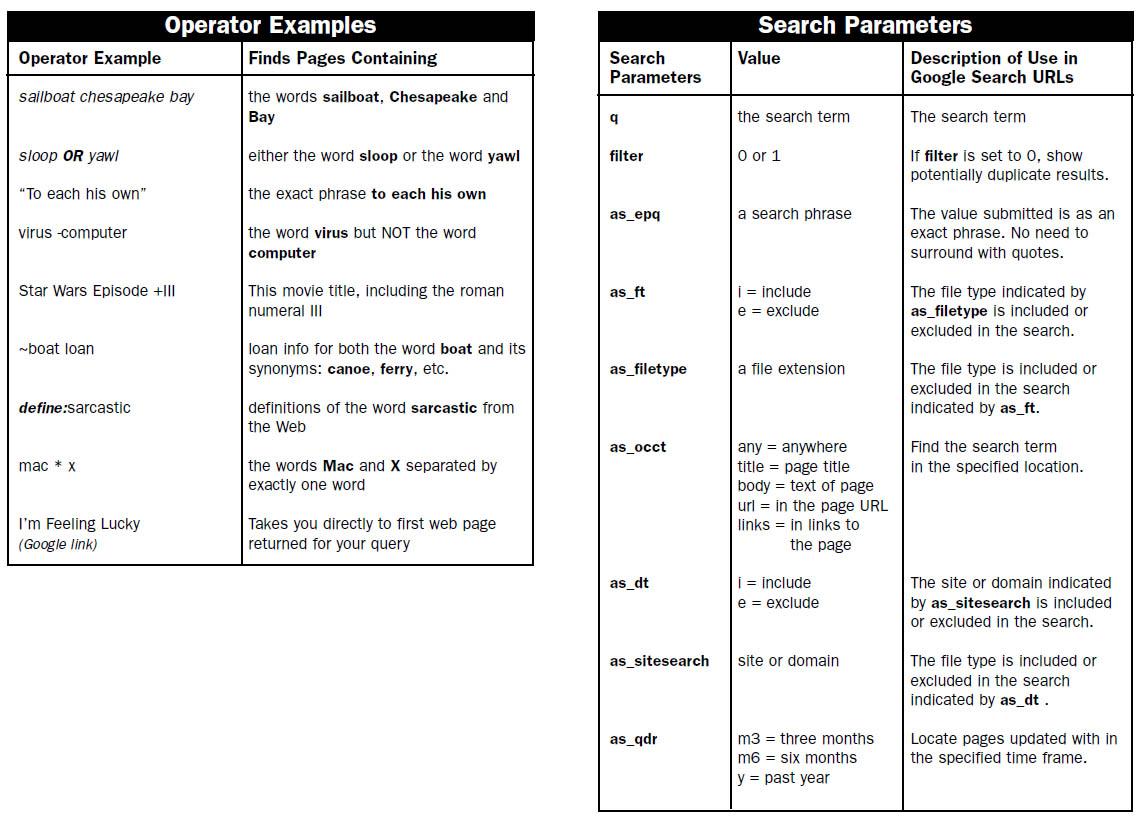
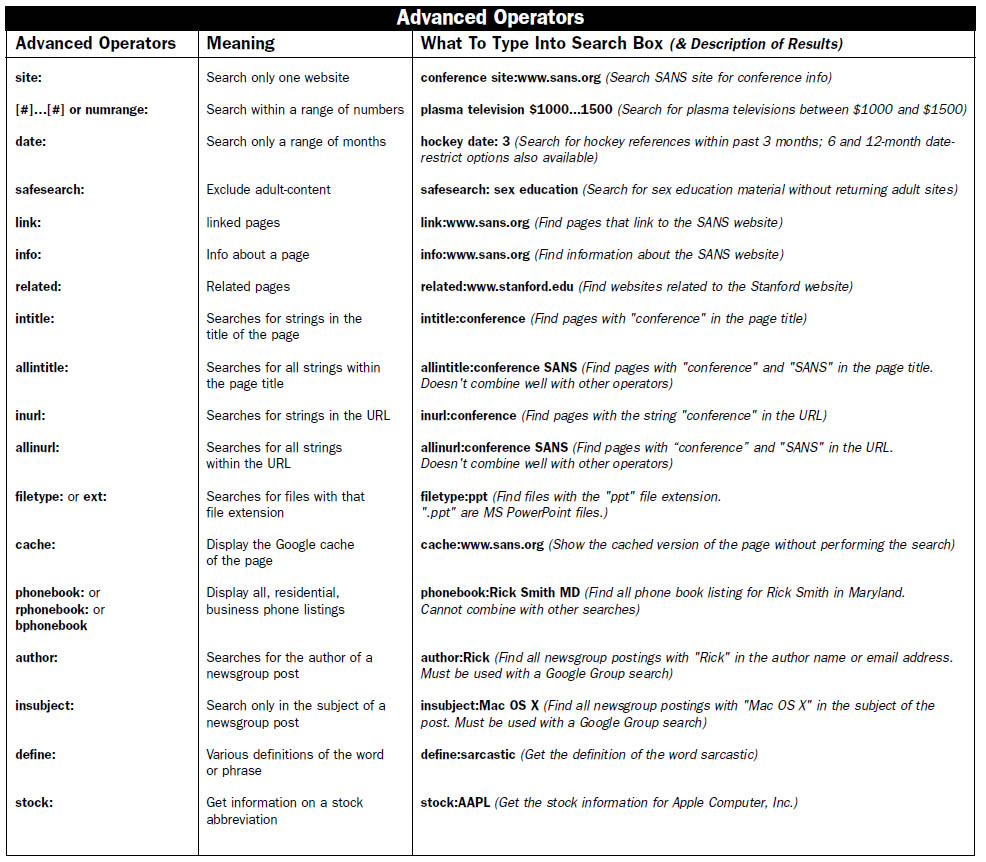
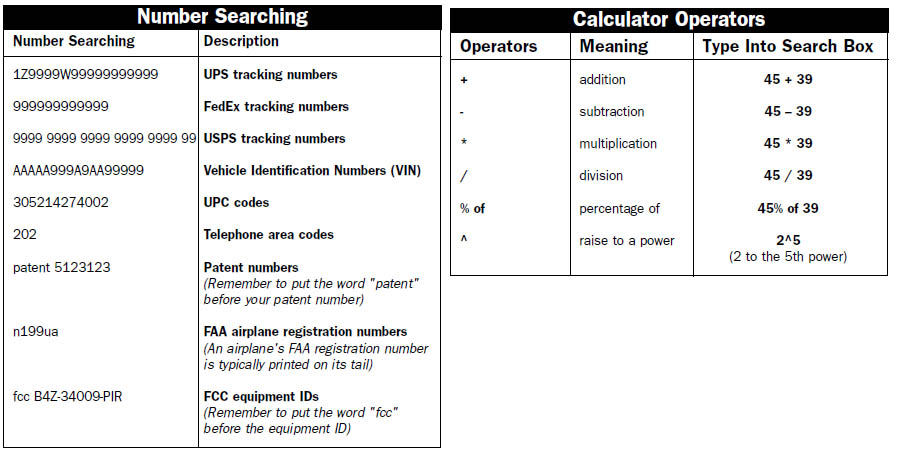
- google hack google dorks database
- nslookup
- shoden
- Netcraft
- shodan
- arin -
- edgar - company registration information
- google hacking - tricks for using google search PDF Book Cheatsheet
- httrack - copy a persons web site
- maltigo
- harvester
- metagoofil
- builtwith.com - Show what a web site was built with
- nslookup - search DNS servers
- Nmap - scan for open ports
- Digg
- insecam - insecure webcams
- hunter.io - find email address
- dcode.fr/tools-list for cryptography like ceasers
- quickcrypto.io convert
- cyptography https://cryptii.com/ can convert encodings
- Cyberchef https://gchq.github.io/CyberChef/
- Encrypt and Decypt with openssl
- https://gchq.github.io/CyberChef/
- hash generators for base64 MD5 SHA1 SHA256 SHA512
- metasploitable server for practicing hacking. login: msfadmin/msfadmin
- Learn Ethical Hacking Tutorials
Attach web application
MetaGooFil
Metagoofil is a Linux based information gathering tool designed for extracting metadata of public documents (.pdf, .doc, .xls, .ppt, .odp, .ods).
Screenshot Here The command to run metagoofil is as follows:
metagoofil.py -d <client domain> -l 100 -f all -o <client domain>.html -t micro-files
The Harvester
TheHarvester is a tool, written by Christian Martorella, that can be used to gather e-mail accounts and subdomain names from different public sources (search engines, pgp key servers). Is a really simple tool, but very effective.
root@pentest:/pentest/enumeration/theharvester# ./theHarvester.py
Examples:./theharvester.py -d microsoft.com -l 500 -b google
./theharvester.py -d microsoft.com -b pgp
./theharvester.py -d microsoft -l 200 -b linkedin
TheHarvester will search the specified data source and return the results. This should be added to the OSINT document for use at a later stage.
root@pentest:/pentest/enumeration/theharvester# ./theHarvester.py -d client.com -b google -l 500
Whois
- ICANN - http://www.icann.org
- IANA - http://www.iana.com
- NRO - http://www.nro.net
- AFRINIC - http://www.afrinic.net
- APNIC - http://www.apnic.net
- ARIN - http://ws.arin.net
- LACNIC - http://www.lacnic.net
- RIPE - http://www.ripe.net
Once the appropriate Registrar was queried we can obtain the Registrant information. There are numerous sites that offer WHOIS information; however for accuracy in documentation, you need to use only the appropriate Registrar.
- InterNIC - http://www.internic.net/ http://www.internic.net]
Nmap
Nmap ("Network Mapper") is the de facto standard for network auditing/scanning. Nmap runs on both Linux and Windows. Nmap is available in both command line and GUI versions. For the sake of this document, we will only cover the command line.
EXAMPLES: nmap -v -A scanme.nmap.org nmap -v -sn 192.168.0.0/16 10.0.0.0/8 nmap -v -iR 10000 -Pn -p 80 SEE THE MAN PAGE (http://nmap.org/book/man.html) FOR MORE OPTIONS AND EXAMPLES
Nmap has dozens of options available. Since this section is dealing with port scanning, we will focus on the commands required to perform this task. It is important to note that the commands utilized depend mainly on the time and number of hosts being scanned. The more hosts or less time that you have to perform this tasks, the less that we will interrogate the host. This will become evident as we continue to discuss the options.
Based on the IP set being assessed you would want to scan both the TCP and UDP ports across the range 1 to 65535. The command that will be utilized is as follows:
nmap -A -PN -sU -sS -T2 -v -p 1-65535 <client ip range>/<CIDR> or <Mask> -oA NMap_FULL_<client ip range>
nmap -A -PN -sU -sS -T2 -v -p 1-65535 client.com -oA NMap_FULL_client Starting Nmap 5.51 ( http://nmap.org ) at 2011-04-22 22:27 Eastern Daylight Time NSE: Loaded 57 scripts for scanning. Initiating Parallel DNS resolution of 1 host. at 22:27 Completed Parallel DNS resolution of 1 host. at 22:27, 0.10s elapsed Initiating SYN Stealth Scan at 22:27 Scanning client.com (74.117.116.73) [65535 ports] Discovered open port 80/tcp on 74.117.116.73
On large IP sets, those greater than 100 IP addresses, do not specify a port range. The command that will be utilized is as follows:
nmap -A -O -PN <client ip range>/<CIDR> or <Mask> -oA NMap_<client ip range>
nmap -A -O -PN client.com -oA NMap_client Starting Nmap 5.51 ( http://nmap.org ) at 2011-04-22 22:37 Eastern Daylight Time Nmap scan report for client.com (74.117.116.73) Host is up (0.13s latency). rDNS record for 74.117.116.73: 74-117-116-73.parked.com Not shown: 999 filtered ports PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.2.3 ((CentOS)) | http-robots.txt: 2 disallowed entries |_/click.php /ud.php |_http-title: client.com |_http-methods: No Allow or Public header in OPTIONS response (status code 200) |_http-favicon: Parked.com domain parking Warning: OSScan results may be unreliable because we could not find at least 1 o pen and 1 closed port Device type: general purpose Running (JUST GUESSING): Linux 2.6.X (92%), OpenBSD 4.X (88%), FreeBSD 6.X (88%)
Google Hacking PDF Cheatsheet
Images