Cybersecurity Masters UVU
Cybersecurity Masters Class Requirements
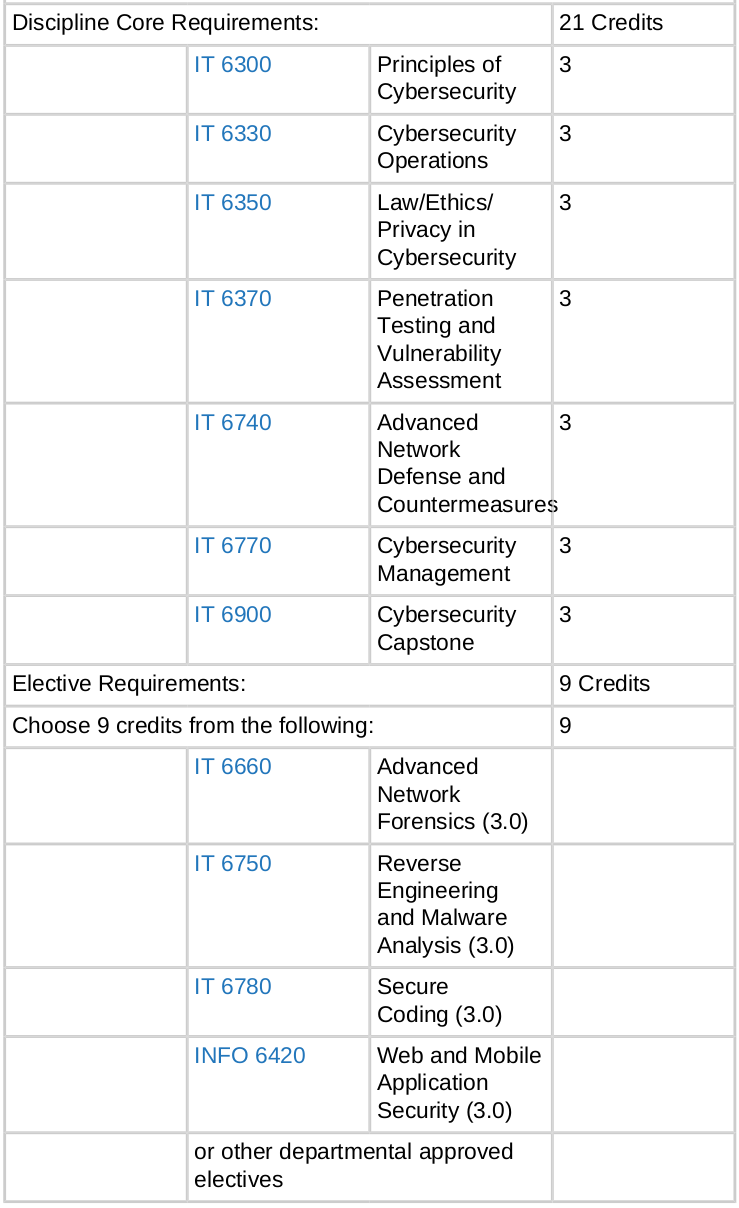
Information Technology Course Descriptions
|
Scripting for Administrators 3:3:0 On Sufficient Demand Prerequisite(s): MAT 1010 or higher; INFO 1120 recommended Introduces the fundamentals of script design and implementation with an emphasis on the automation of administrative tasks. Covers modular script design and the use of file input and output. Emphasizes interaction of a script with other scripts, utilities, and the operating system to form more complex systems. Manipulates values of variables (both numbers and strings). Introduces simple GUI interfaces. Introduction to System Administration--Linux/UNIX 3:3:0 Fall, Spring, Summer Prerequisite(s): INFO 1120 recommended Introduces the UNIX Operating System using the popular Linux OS. Explores the Linux file system, Linux administration, OS utilities, and program features and uses. Aids the student in the development, understanding, and working knowledge of the details of the Linux Operating System, memory organization, disk architectures, and demand paged virtual memory. Includes OS installation, user creation, rights management, loading daemons, and server best practices. Lab access fee of $35 for computers applies. Computer Architecture and Systems Software 3:3:0 Fall, Spring, Summer Prerequisite(s): INFO 1120 recommended Provides a thorough grounding in computer hardware, system software, and contemporary information system architecture. Examines hardware structure, operating systems theory, and systems software as part of a technical foundation for enterprise systems development and IT infrastructure procurement and management. Lab access fee of $35 for computers applies. Cybersecurity Essentials 3:3:0 On Sufficient Demand For non-Information Technology and non-Information Systems majors. Introduces cybersecurity and its role in society in a nontechnical way. Explores cybersecurity topics, including protecting accounts, securing data, and avoiding phishing scams. Discusses current hacking and cybersecurity events. Identifies best practices for personal cybersecurity. Provides basic introduction to cybersecurity tools. Voice and Data Cabling Fundamentals 3:3:0 Fall, Spring, Summer Prerequisite(s): INFO 1120 or INFO 1200 or CS 1030 or CS 1400 For students interested in the physical aspects of voice and data network cabling and installation. Focuses on cabling issues related to data and voice connections and provides an understanding of the industry and its worldwide standards. Covers types of media and cabling, physical and logical networks, as well as signal transmission. Focuses on best practices and safety using copper and fiber-optic cabling. Requires students to install a complete cable infrastructure for a simulated telecommunications room. Enforces industry and worldwide standards. Requires a community project and portfolio based on voice/data cabling skills. Lab access fee of $35 for computers applies. Introduction to System Administration--WIndows Client 3:3:0 Fall, Spring Prerequisite(s): IT 1600 Introduces operation management of operating systems using Microsoft Windows. Introduces installation methods and troubleshooting, hardware device installation and management, storage management, disaster recovery planning and management. Aids the student in the development, understanding, and working knowledge of the Windows networking framework including peer-to-peer, workgroups, user profiles, domains, NTFS, and share-level permissions. Lab access fee of $35 for computers applies. Data Communication Fundamentals 3:3:0 Fall, Spring, Summer Prerequisite(s): INFO 1120 recommended or IT 1600 recommended or CS 1400 recommended Provides an in-depth knowledge of data communications and enterprise networking including networking and telecommunications technologies, hardware, and software. Emphasizes underlying technologies and protocols. Design topics include wired and wireless architectures; topologies, models, standards and protocols; and operation of bridges, routers, switches, and gateways. Includes lab assignments covering TCP/IP implementations. May be delivered hybrid. Lab access fee of $35 for computers applies. Information Security Fundamentals 3:3:0 Fall, Spring, Summer Prerequisite(s): IT 2600 or CS 2600; (IT 1600 recommended) Explores introductory information and cybersecurity concepts: security technologies, methodologies, and tools. Topics include security models, risk assessment, threat analysis, attack types, encryption technologies, security implementation, access controls, business continuity, and security policies. Discusses current topics, trends, and career opportunities in information security. Includes lab assignments covering information security principles. Software fee of $18 applies. Lab access fee of $35 for computers applies. Computer Forensic Fundamentals 3:3:0 Fall, Spring, Summer Prerequisite(s): INFO 1120 or IT 1600 or CS 1400 or CJ 1010 Explores procedures for identification, preservation, and extraction of electronic evidence. Emphasizes auditing and investigation of network and host system intrusions, analysis and documentation of information gathered, and preparation of expert testimonial evidence. Examines forensic tools and resources for system administrators and information system security officers. Includes ethics, law, policy, and standards concerning digital evidence. Requires lab experience and a research paper or project. Lab access fee of $35 for computers applies. Internship 1 to 4:0:5 to 20 On Sufficient Demand Prerequisite(s): Department Approval Provides opportunities to apply classroom theory on the job. Requires work as paid employees in a job that relates to their careers while enrolled at the university. Requires students to meet at least monthly with the Departmental Internship Coordinator. Requires completers to meet individually set goals. May be repeated for a maximum of three credits toward graduation. May be graded credit/no credit. Current Topics in Information Technology 1 to 3:1 to 3:0 On Sufficient Demand Prerequisite(s): Departmental Approval Provides exposure to current and emerging information technologies. May be used to provide content to prepare students to take industry-recognized IT certification exams, such as CompTIA Linux+, CompTIA A+, Apple Certificated Professional, Certified Fiber Optic Technician, IC3, CompTIA Network+, CompTIA CTP+, Access Data Certified Examiner, MCSA, Cisco CompTIA Security+, Certified Ethical Hacker, etc. Varies each semester. May be repeated for a maximum of 6 credits toward graduation. Lab access fee of $35 for computers applies. Intellectual Property and Cyber Law 3:3:0 Fall, Summer Prerequisite(s): (ENGL 2010 or ENGL 2020) and (PRLG 1000 or CS 1030 or INFO 1120 or LEGL 3000) and University Advanced Standing Focuses on trademarks, copyrights, patents, and unfair competition, and examines legal requirements to create, register and protect intellectual property rights. Examines domestic and international trends in this developing legal area. Teaches legislation and case law concerning technology, professional responsibilities, risks, and liabilities. Discusses intellectual property rights and responsibilities pertaining to technology. Lab access fee of $35 for computers applies. Data Cabling Signal Characteristics 3:3:0 On Sufficient Demand Prerequisite(s): INFO 1120 or INFO 1200 or CS 1030 or CS 1400 or MECH 1200 For EART/Mechatronics majors or students interested in the physical aspects of data network signal characteristics, cabling and installation for those signals. Focuses on cabling issues related to data and voice connections and provides an understanding of the industry and its worldwide standards. Covers types of media and cabling, physical and logical networks, as well as signal transmission. Focuses on best practices and safety using copper and fiber-optic cabling. Requires students to install a complete cable infrastructure for a simulated telecommunications room. Enforces industry and worldwide standards. Requires a community project and portfolio based on voice/data cabling skills. Requires a research paper. Advanced System Administration--Linux/UNIX 3:3:0 Fall, Spring, Summer Prerequisite(s): [INFO 1200 and IT 1510 and (IT 2600 or CS 2600) all with a grade of C- or higher within the past five years] and University Advanced Standing Explores enterprise systems administration using the UNIX/Linux operating system. Students learn advanced administrative tasks including server installation, network configuration and user management, file management, network services deployment, server security, back up and recovery, Shell scripting, source compilation, performance monitoring and tuning, troubleshooting, and managing hardware and component changes. Requires a community project and portfolio based on advanced server management skills. Lab access fee of $35 for computers applies. Advanced System Administration--Windows Server 3:3:0 Fall, Spring, Summer Prerequisite(s): [INFO 1200 and IT 2530 and (IT 2600 or CS 2600) all with a grade of C- or higher within the past five years] and University Advanced Standing Explores enterprise systems administration using the Microsoft Windows Server operating system. Students learn advanced administrative tasks including server installation; hardware change management; software application management; network configuration and user management; file management; printing; network services deployment; server security; back up and recovery; scripting; performance monitoring, tuning, and troubleshooting. Lab access fee of $35 for computers applies. Mac OS and Server Support 3:3:0 Fall, Spring, Summer Prerequisite(s): [INFO 1200 and IT 1510 and (IT 2600 or CS 2600) all with a grade of C- or higher within the past five years] and University Advanced Standing Provides an in-depth exploration of the Mac OS X, and provides the skills to troubleshoot and correct problems that may arise by users. Teaches installation and configuration of a Mac OS X Server. Involves implementing and maintaining a Mac server in a network, including file sharing, mail, web, and wikis. Software fee of $14 applies. Lab access fee of $35 for computers applies. Internetworking and Router Management 3:3:0 Fall, Spring, Summer Prerequisite(s): [(INFO 1200 or CS 1400) and (IT 2600 or CS 2600) all with a grade of C- or higher within the past five years] and University Advanced Standing Teaches the theory and implementation skills and techniques needed to configure, troubleshoot and support reliable TCP/IP internetworks. Discusses security and management issues. Offers the opportunity to build an internetwork with cables, network cards, and routers. Emphasizes the analysis and design of networks in organizations. Includes lab assignments covering TCP/IP implementations and router configurations. Lab access fee of $35 for computers applies. Information Storage and Management 3:3:0 On Sufficient Demand Prerequisite(s): IT 1600, IT 2600, and University Advanced Standing Presents concepts, principles, and deployment considerations across all technologies that are used for storing and managing information. Describes challenges and solutions for data storage and data management, intelligent storage systems, and storage networking. Studies backup, recovery, and archive processes. Discusses business continuity, disaster recovery, storage security and virtualization, and managing and monitoring the storage infrastructure. Software fee of $192 applies. Lab access fee of $35 for computers applies. Information Security--Network Defense and Countermeasures 3:3:0 Fall, Spring, Summer Prerequisite(s): IT 1510, IT 2700, (IT 3510 or IT 3530), and University Advanced Standing Prerequisite(s) or Corequisite(s): IT 3600 Examines advanced information security concepts through an applied viewpoint. Extends the student's understanding of security issues through hands-on application of real-world techniques and use of current security software. Topics include legal/ethical issues, use of security tools, network reconnaissance, password/brute-force attacks, firewall configuration, Honeypot deployment, intrusion analysis/detection, server hardening, and penetration testing. Guest lecturers provide insight into current trends in advanced security issues. Software fee of $18 applies. Lab access fee of $35 for computers applies. Current Topics in Information Technology 3:3:0 On Sufficient Demand Prerequisite(s): (Junior Standing or Department Approval) and University Advanced Standing Provides exposure to emerging technologies and topics of current interest in information technology. Varies each semester depending upon the changes in the information technology discipline or to address a focused area within the information technology discipline. May be repeated for a maximum of 9 credits toward graduation. Lab access fee of $35 for computers applies.
|
Enterprise Network Architectures and Administration 3:3:0 Fall, Spring, Summer Prerequisite(s): IT 3600 and University Advanced Standing Examines management of resources used in enterprise computing environments from a practical, applied viewpoint. Extends the student's understanding of these concepts through hands-on application of real-world network, server, and software management techniques and addresses the problems associated with providing a secure, stable, reliable enterprise computing infrastructure. Includes principles of IT enterprise infrastructure management; configuration, analysis, and troubleshooting of virtual servers; redundancy and failover; directory service integration, access control and security; uptime monitoring and notification; backup and recovery; Storage Area Networking; Cloud computing platform choices, functionality, cost, deployment, flexibility, and adaptability. Lab access fee of $35 for computers applies. Software fee of $118 applies. Enterprise Information Security Management 3:3:0 Fall, Spring, Summer Prerequisite(s): IT 2700 and University Advanced Standing Prerequisite(s) or Corequisite(s): INFO 3430 Provides perspective of key issues involved in IT activities across the organizational and technical security landscape. Examines management methodologies, staffing, and operational issues. Teaches use of financial analysis and decision-making methodologies to aid investment decisions at the operational, functional, and strategic levels. Illustrates use of risk assessment and contingency planning as applied to business continuity and disaster recovery strategies. Includes the use of Service Level Agreement for managing both internal and external relationships. Lab access fee of $35 for computers applies. Network Security and Operations Capstone 3:3:0 Fall, Spring Prerequisite(s): University Advanced Standing Prerequisite(s) or Corequisite(s): IT 4700 Senior-level, capstone experience course. Enhances student cyber security knowledge with operational and business applications. Focuses on integrating cyber security principles as an organic part of an organization's processes. Covers barriers to implementing security policy, building a business case for cyber security, and incorporating cyber security into project management and software life cycles. Requires student project presentations. Lab access fee of $35 for computers applies. Case Studies in Cyber Security 3:3:0 On Sufficient Demand Prerequisite(s): IT 2700 and University Advanced Standing Discusses current trends and issues in cyber security. Updated regularly to reflect global events related to cyber security. Topics include data breaches, cyber warfare, emerging threats. Emphasis on the changing and transformative nature of cyber security threats, including geographical, institutional, and cultural evolution. Guest lecturers from industry will provide students with perspectives on the state of cyber security. Examines real-world examples of the application of cyber security principles and requires critical analysis of each case. Lab access fee of $35 for computers applies. Advanced Mobile Devices Forensics 3:3:0 Spring Prerequisite(s): (IT 2800 or FSCI 3800) and University Advanced Standing; IT 3540 recommended A continuation of IT 2800. Teaches students about additional devices that can store digital information. Exposes students to devices such as cell phones, PDAs, Tablets, MP3 players, digital camera/camcorders, and GPS units. Includes lab investigations of one or more digital media through image acquisition, data recovery, and assembly of a final written report of findings. Requires students to use multiple software tools in device acquisition and analysis. Includes weekly written papers covering topics in the field of digital forensics. Lab access fee of $35 for computers applies. Internship 1 to 8:0:5 to 40 Fall, Spring, Summer Prerequisite(s): (IT 3510 or IT 3530 or IT 3540 or IT 3600 or IT 3700 or department approval) and University Advanced Standing For Information Technology bachelor's degree students. Provides opportunities to apply upper-division classroom theory while students work as employees in a job that relates to their careers. Meet periodically with a Departmental Internship Coordinator. Credit is determined by the number of hours a student works during the semester and completion of individually set goals that relate to the student's selected emphasis. Prior written department chair approval is required to apply more than three credits toward a Bachelor of Science Degree in Information Technology. May be graded credit/no credit. Digital Forensics Investigations 3:3:0 On Sufficient Demand Prerequisite(s): (IT 2800 or FSCI 3800) and University Advanced Standing Prerequisite(s) or Corequisite(s): FSCI 3400 Senior Capstone course for students in the Computer Forensics emphasis. Covers one or more investigations from start to finish. Integrates knowledge and skills from previous CJ, FSCI, and IT courses in this culminating experience. Lab access fee of $35 for computers applies. Undergraduate Research in Information Technology 1 to 4:0:5 to 20 On Sufficient Demand Prerequisite(s): Department approval and University Advanced Standing Provides the opportunity to conduct research under the mentorship of a faculty member. Practices the theoretical knowledge gained in prior major courses. Creates a significant intellectual or creative product that is characteristic of the Information Technology discipline and worthy of communication to a broader audience. May be repeated for a maximum of 6 credits toward graduation. Independent Study 1 to 3:0:3 to 9 On Sufficient Demand Prerequisite(s): Department chair approval and University Advanced Standing For bachelor degree students and other interested persons. Offers independent study as directed in reading, in individual projects, at the discretion and approval of the department chairperson. May be repeated for a maximum of 9 credits toward graduation. Principles of Cybersecurity 3:3:0 Fall Prerequisite(s): Acceptance into Graduate Certificate or Master of Science in Cybersecurity or Departmental Approval Provides foundational knowledge of cybersecurity for graduate-level studies. Covers information security theories, terminology, and implementation. Includes networking and system fundamentals, cryptography, malware, authentication, authorization, access control, physical security, attacker profiles, appropriate threat responses, and the human elements of cybersecurity. Introduces multiple aspects of cybersecurity and various career paths within the field. Cybersecurity Operations 3:3:0 Fall Prerequisite(s): Acceptance into Graduate Certificate or Master of Science in Cybersecurity or Departmental Approval Focuses on operational aspects of cybersecurity. Includes incident response, network monitoring, change management, configuration management, and resource protection. Emphasizes the role of cybersecurity in the enterprise. Integrates sound cybersecurity principles into various aspects of IT operations. Includes information on secure server administration and open source security software. Teaches cybersecurity standards for government and industry sources and the application of those standards. Law/Ethics/Privacy in Cybersecurity 3:3:0 Spring Prerequisite(s): Acceptance into Graduate Certificate or Master of Science in Cybersecurity or Departmental Approval Explores legal, ethical, and privacy issues as they apply to cybersecurity. Includes the legalities and ethics of hacking, corporate information security and use policies, and the government's role in cybersecurity. Emphasizes the roles and responsibilities of individual cybersecurity practitioners as well as corporate entities, including vulnerability disclosure and correcting software defects. Teaches privacy policies and regulations as they relate to cybersecurity and information systems. Penetration Testing and Vulnerability Assessment 3:3:0 Summer Prerequisite(s): Acceptance into Graduate Certificate or Master of Science in Cybersecurity or Departmental Approval Prerequisite(s) or Corequisite(s): IT 6300 Explores advanced topics in ethical hacking, penetration testing, vulnerability assessment, and other offensive network and system techniques. Teaches network scanning, target identification, application exploitation, antivirus evasion, physical security, social engineering, phishing, and privilege escalation. Contains hands-on labs providing experience from the perspective of an attacker. Advanced Network Forensics 3:3:0 On Sufficient Demand Prerequisite(s): Acceptance into Graduate Certificate or Master of Science in Cybersecurity or Departmental Approval Prerequisite(s) or Corequisite(s): IT 6300 Provides a standard methodology for conducting digital forensic analysis in a network environment. Teaches the importance of network forensic principles and development of an understanding of the technologies, protocols, laws, regulations, ethics, and procedures for network forensics. Incorporates demonstrations and laboratory exercises covering the identification, acquisition, authentication, preservation, analysis, and reporting of evidence for prosecution purposes. Advanced Network Defense and Countermeasures 3:3:0 Spring Prerequisite(s): Acceptance into Graduate Certificate or Master of Science in Cybersecurity or Departmental Approval Prerequisite(s) or Corequisite(s): IT 6300 Explores advanced topics in network defense, server hardening, vulnerability assessment, and mitigation scanning. Teaches students about network scanning, asset identification, Linux and Windows server hardening, anti-malware tools, intrusion detection, physical security, perimeter security, and cybersecurity awareness training. Contains hands-on labs providing experience from the perspective of a defender. Lab access fee of $35 for computers applies. Reverse Engineering and Malware Analysis 3:3:0 On Sufficient Demand Prerequisite(s): Acceptance into Graduate Certificate or Master of Science in Cybersecurity or Departmental Approval Prerequisite(s) or Corequisite(s): IT 6300 Explores the analysis tools and techniques for identifying malicious programs and recovering compromised operating systems. Provides a standard methodology for reverse engineering and eradicating malware. Includes setting up isolated malware labs and utilizing a selected set of forensic tools, such as system and network monitoring utilities, disassemblers, and debuggers for analyzing malware characteristics and the impact that malware may have on compromised systems. Case Studies in Cybersecurity 3:3:0 On Sufficient Demand Prerequisite(s): Acceptance into Graduate Certificate or Master of Science in Cybersecurity or Departmental Approvall Prerequisite(s) or Corequisite(s): IT 6300 Discusses current trends and issues in cybersecurity. Reflects current global events related to cybersecurity. Includes data breaches, cyber warfare, and emerging threats. Emphasizes the changing and transformative nature of cybersecurity threats, including geographical, institutional, and cultural evolution. Provides guest lecturers from industry with perspectives on the state of cybersecurity. Examines real-world examples of the application of cybersecurity principles and requires critical analysis of each case. Lab access fee of $35 for computers applies. Cybersecurity Management 3:3:0 Summer Prerequisite(s): IT 6300 or Departmental approval Teaches management skills applicable to cybersecurity. Includes governance models, business continuity, disaster recovery, risk management, organizational security, cybersecurity life cycle management, and interactions between information technology and business units. Focuses on policies, procedures, and guidelines based on industry and government standards to fulfill legal, regulatory, and operational requirements. Lab access fee of $35 for computers applies. Secure Coding 3:3:0 Fall Prerequisite(s): IT 6300 or departmental approvall Focuses on fundamentals of secure coding and current topics in application security. Includes the implementation of secure development lifecycle principles, identifying and mitigating issues in existing applications, and common security issues. Covers the most frequently encountered application security risks and how to address each of them. Includes web applications, mobile applications, and traditional desktop applications. Lab access fee of $35 for computers applies. Cybersecurity Capstone 3:3:0 Spring Prerequisite(s): IT 6330, IT 6350, IT 6370, IT 6740, and IT 6770 Provides culmination of cybersecurity in a self-directed research or practical project that showcases student's mastery of cybersecurity topics. Provides an opportunity to conduct research and/or implement systems that incorporate topics from previous courses. Requires students to present their work at the end of the semester. |
2018-19 Master of Science in Cybersecurity--Tuition and Fee Schedule
| Resident | Non-Resident | |||||||
| Credit Hours | Tuition | Fees | Total | Credit Hours | Tuition | Fees | Total | |
| 1 | $406 | $35 | $441 | 1 | $986 | $35 | $1,021 | |
| 2 | $812 | $70 | $882 | 2 | $1,972 | $70 | $2,042 | |
| 3 | $1,218 | $105 | $1,323 | 3 | $2,958 | $105 | $3,063 | |
| 4 | $1,624 | $140 | $1,764 | 4 | $3,944 | $140 | $4,084 | |
| 5 | $2,030 | $175 | $2,205 | 5 | $4,930 | $175 | $5,105 | |
| 6 | $2,436 | $210 | $2,646 | 6 | $5,916 | $210 | $6,126 | |
| 7 | $2,842 | $245 | $3,087 | 7 | $6,902 | $245 | $7,147 | |
| 8 | $3,248 | $280 | $3,528 | 8 | $7,888 | $280 | $8,168 | |
| 9 | $3,654 | $315 | $3,969 | 9 | $8,874 | $315 | $9,189 | |
| 10 | $4,060 | $350 | $4,410 | 10 | $9,860 | $350 | $10,210 | |
| 11 | $4,466 | $350 | $4,816 | 11 | $10,846 | $350 | $11,196 | |
| 12 | $4,872 | $350 | $5,222 | 12 | $11,832 | $350 | $12,182 | |
| 13 | $5,278 | $350 | $5,628 | 13 | $12,818 | $350 | $13,168 | |
| 14 | $5,684 | $350 | $6,034 | 14 | $13,804 | $350 | $14,154 | |
| 15 | $6,090 | $350 | $6,440 | 15 | $14,790 | $350 | $15,140 | |
| 16 | $6,496 | $350 | $6,846 | 16 | $15,776 | $350 | $16,126 | |
| 17 | $6,902 | $350 | $7,252 | 17 | $16,762 | $350 | $17,112 | |
| 18 | $7,308 | $350 | $7,658 | 18 | $17,748 | $350 | $18,098 | |
| 19 | $7,714 | $350 | $8,064 | 19 | $18,734 | $350 | $19,084 | |
| 20 | $8,120 | $350 | $8,470 | 20 | $19,720 | $350 | $20,070 | |
Professors
Cybersecurity Advisory Board
- Dan Anderson, Consultant, Spectra
- Vance Checketts, High-Tech COO, Dell EMC2
- David Glod, VP of Information Security, Mountain America Credit Union
- Gary Glover, Director of Security Assessments, SecurityMetrics, Inc.
- Steve Leyba, Service Area Director, Department of Workforce Services
- Angela Madsen, Operations Manager, Department of Workforce Services
- Robert Schroader, President, CEO, Paraben Corporation
- Justin Searle, Managing Partner, UtiliSec
Books for the Classes
These were the books when I took the courses
IT 6300
- The Basics of Information Security (
second edition). Jason Andress. Syngr ess 2014 - Information Security: Principles and Practices (second edition). Sari Stern Greene. Pearson 2014
IT 6330
Designing and Building a Security Operations Center
By: David Nathans
Publisher: Syngress
Pub. Date: November 6, 2014
Print ISBN-13: 978-0-12-800899-7
Cyber Operations: Building, Defending, and Attacking Modern Computer Networks
By: Mike O’ Leary
Publisher: Apress
Pub. Date: November 4, 2015
Print ISBN-13: 978-1-4842-0458-0
Security Operations Center: Building, Operating, and Maintaining your SOC
By: Gary McIntyre; Nadhem AlFardan; Joseph Muniz
Publisher: Cisco Press
Pub. Date: October 29, 2015
Print ISBN-10: 0-13-405201-3
Print ISBN-13: 978-0-13-405201-4
Ten Strategies of a World-Class Cybersecurity Operations Center
By:Carson Zimmerman
Publisher: The MITRE Corporation
Pub. Date: 2014
ISBN: 978-0-692-24310-7
IT 6350
- No text book, all material were given in the form of current cyber security case studies
IT 6370
- Metasploit: The Penetration Tester's Guide
David Kennedy, Jim O’Gorman, Devon Kearns, and Mati Aharoni
July 2011, 328 pp.
ISBN-13:
978-1-59327-288-3
IT 6740
- No text book
IT 6770
- The Security Risk Assessment Handbook (2nd Edition). Douglas Landoll. CRC Press
All the books were available for free, either through safari books online or just through other sources.
