Strategy 4: Do a Few Things Well
Our primary objective is to limit capability “sprawl” so we can focus on doing a few things well rather than many poorly.
Introduction
Capability Templates
SOC templates we described in Section 4.1.2, using the following descriptors:
B: Basic. The SOC has a partial or basic capability in this area.
A: Advanced. The SOC has a well-developed, mature capability in this area.
O: Optional. The SOC may or may not offer this capability, potentially deferring it to an external group either within the constituency or from another SOC, if appropriate.
–: Not Recommended. Usually due to constituency size or distance from end assets and mission, it is not recommended that the SOC support this capability.
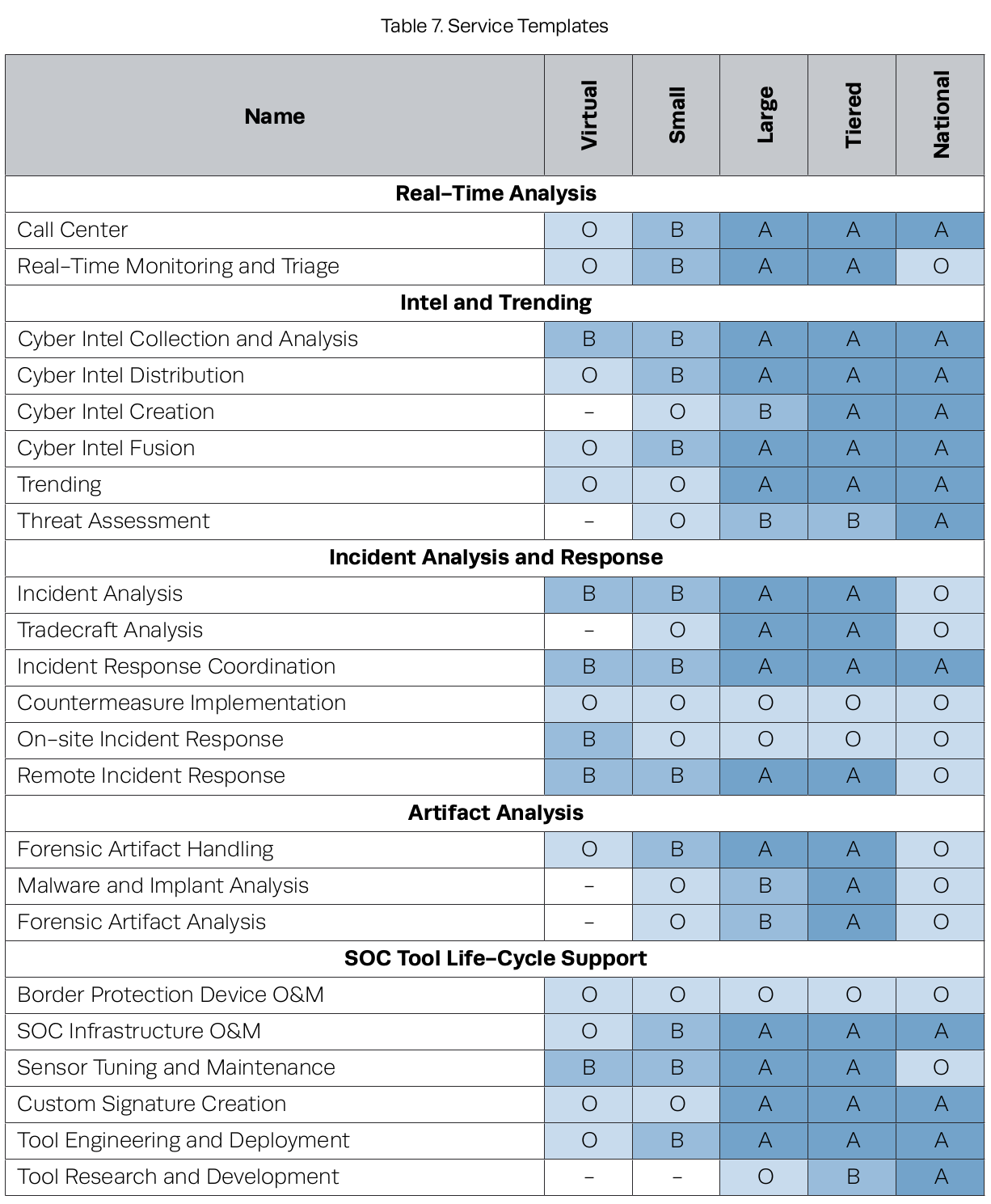
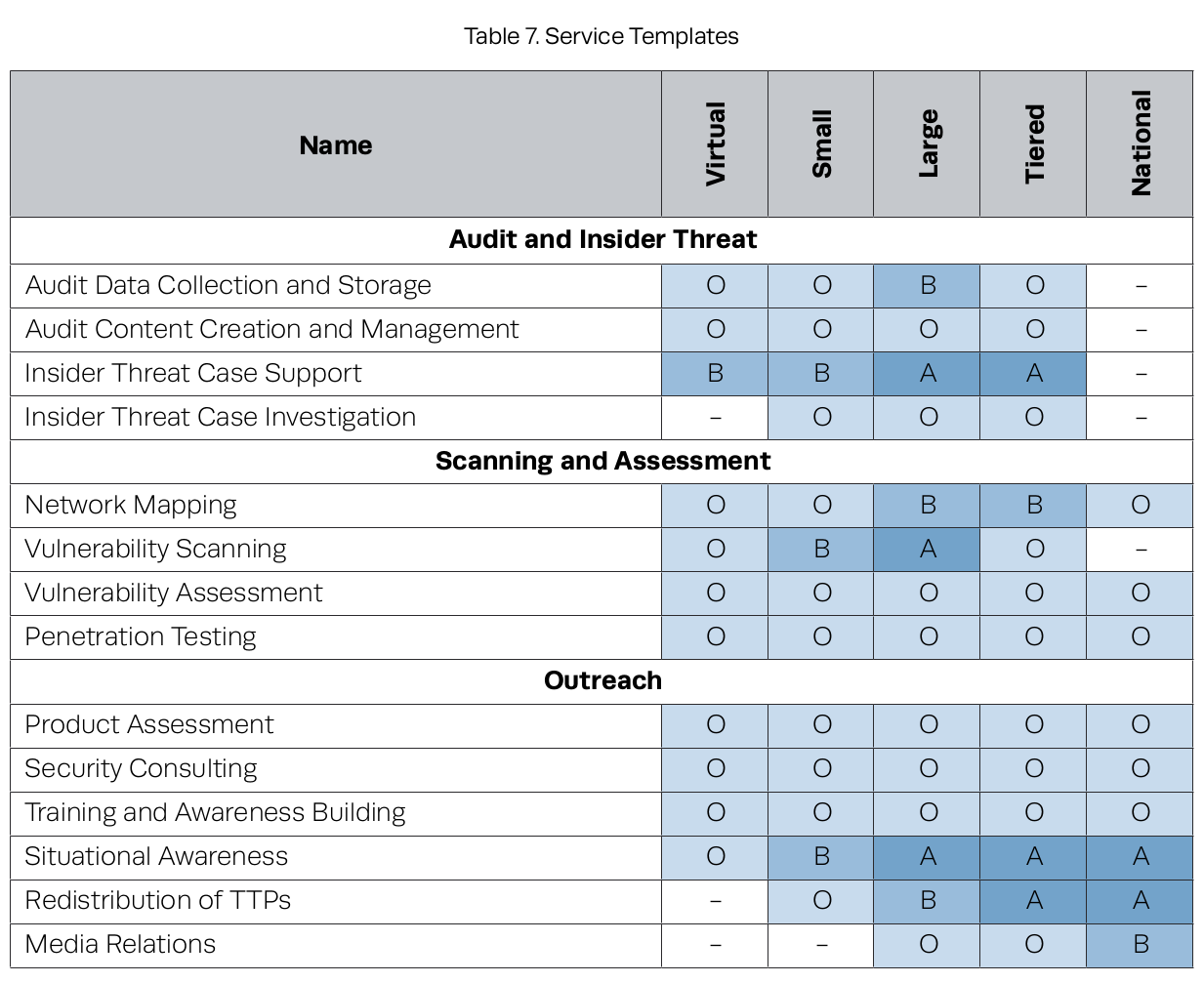
Some major decision points:
Call center. Small SOCs may transfer this function to either the help desk or the NOC.
Real-time monitoring and triage/incident analysis. This capability is core to virtu-
ally all SOCs.
Malware and implant analysis/forensic artifact analysis. These capabilities are
hard to staff in small and medium-sized SOCs for two reasons:
- There needs to be a steady stream of incidents requiring in-depth postmortem, attribution, or legal action
- Personnel qualified to do this are in high demand. It is effective for a smaller SOC to rely on a service provider.
Sensor tuning. If a SOC has its own fleet of monitoring equipment (e.g., network or host IDS/IPS), tuning must be a sustained, internal activity driven by feedback from analysts. Therefore, this capability is considered a requirement for any SOC that deploys monitoring capabilities.
Tool engineering and deployment. Whether a SOC performs this in house or depends
on an external organization, this capability must exist somewhere
Vulnerability assessment and penetration testing. The SOC is a natural place to house and coordinate these activities. It provides a unique basis for enhanced SA and raises visibility of the SOC as a resource to system owners and security staff. Some smaller constituencies may outsource this to a third party.
Network mapping/vulnerability scanning. These capabilities may be viewed as sustaining IT functions rather than CND or security operations functions.
Border protection device O&M/countermeasure implementation. These capabilities are rarely offered by a SOC that is not organizationally adjacent to, or comingled with, IT/network operations, as in a NOSC.
Audit data collection, retention, and management.
These capabilities are likely seen as a side benefit of comprehensive log collection and analysis.
Capability Maturation
