Strategy 7: Exercise Discrimination in the Data You Gather
9.1 Sensor Placement
- Passive network sensors, including general-purpose NIDS
- Active network sensors: NIPS and content detonation devices
- Application-specific protection appliances (XML, database, etc.).
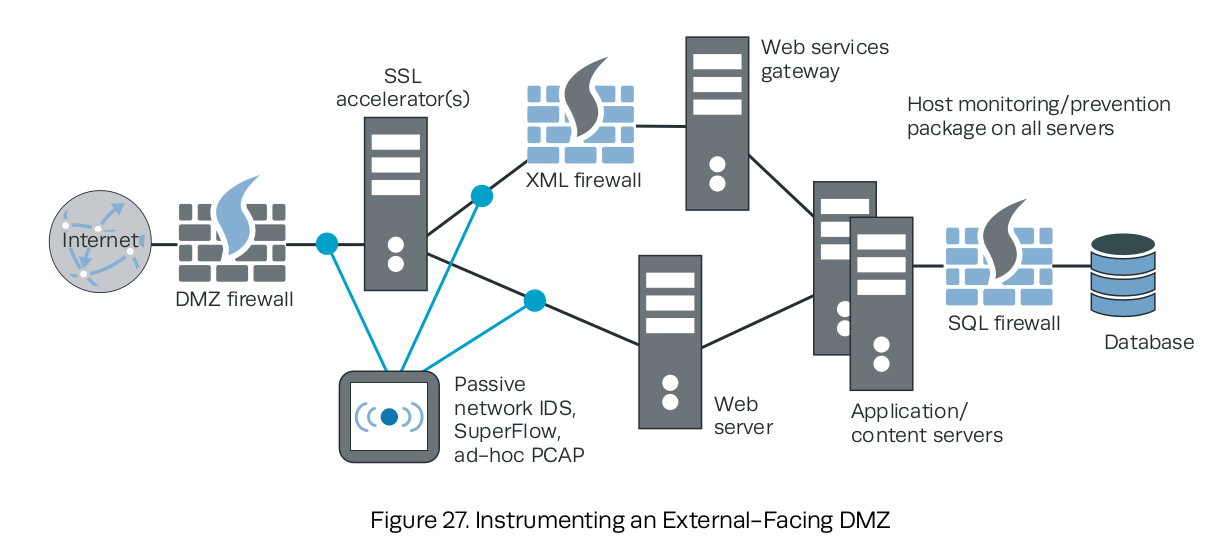
9.2 Selecting and Instrumenting Data Sources
Drivers for collection of IT security log data:
- Computer network defense
- Insider threat monitoring and audit collection
- Performance monitoring
- Maintenance troubleshooting and root-cause analysis
- Configuration management.
User attribution is hard. Attaining probable or confirmed connections to people’s actions is a big part of running incidents to ground.
Don’t log just the “denies”; the “allows” are often just as important.
