Strategy 6: Maximize the Value of Technology Purchases
Write a short paper discussing the challenges facing organizations when choosing technology. You should include other sources in addition to the Mitre book.
What are you paying your cyber security for? You are paying them to make sure things don't happen.
What damage could happen? How likely is it to happen? How much will it cost to mitigate?
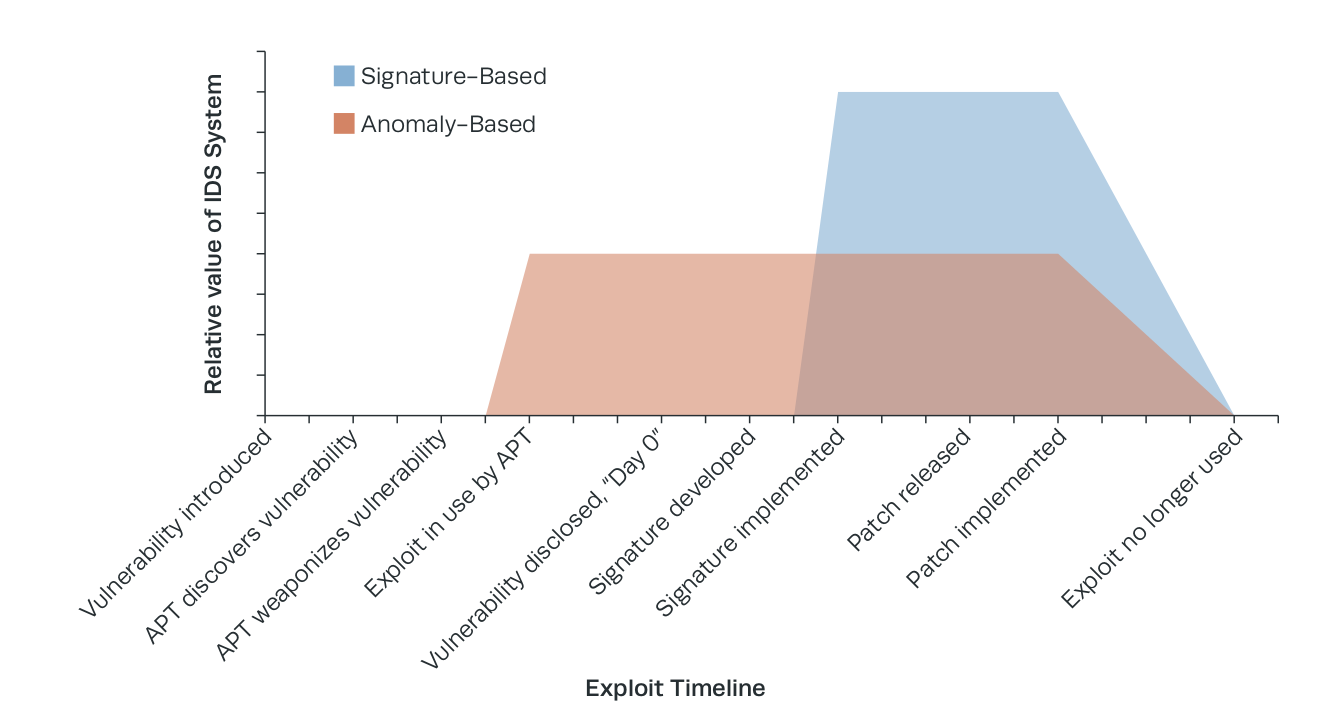
- What are the advantages of Behavior-based or anomaly detection in an IDS?
- What are the advantages of Knowledge-based or signature-based detection in an IDS?
- What can be done or used to shorten timelines for incident analysis from weeks and months to minutes and hours?
Find the balance between the hassle of the protection and the likely-hood that you will use that protection.
Whys to handle Risk (example driving down the freeway)
- Mitigation - drive careful, wear seat-belt
- Transfer - Insurance
- Avoidance - Don't drive on the freeway
- Acceptance -
Cost-effective technologies needed to mount a competent defense of the enterprise are widely available; issues of people and process are usually what hold SOCs back from using them effectively.
In our sixth strategy, our goal is to extract the maximum value from each technology purchase we make, with respect to the adversary and the SOC mission.
The tools in CND.
- Vulnerability scanners and network mapping systems
- NIDS/NIPS, which are used as tip-offs to user, system, or network behavior that is of concern
- Complements to NIDS/NIPS, including NetFlow (which records a summary of network activity), full-session network capture collection, and content detonation devices (which inspect documents and Web pages for malicious behavior)
- The host counterpart to NIDS, HIDS/HIPS, which, in many cases, also include various enhancements and add-on modules such as AV and configuration monitoring Ten Strategies of a World-Class Cybersecurity Operations Center 109
- A means of gathering, normalizing, correlating, storing, and presenting events from these various sources, such as a SIEM system and its less expensive counterpart, Log Management (LM) Appliances.
We should:
- Maintain cognizance over the entire threat landscape and what is most relevant to the constituency—what will be the most damaging, and which are most likely to occur.
- Consider the overall value of each tool in terms of visibility, cyber attack life cycle coverage, and longevity.
- Focus on a discrete set of tools that provide maximum value and avoid overlap in functionality where redundancy is not needed.
- Pursue a rigorous requirements-driven approach based on operator feedback.
- Carefully manage expectations of IT executives regarding the virtues and limitations of tools under consideration—there is no panacea.
- Ensure the SOC has the expertise to exploit the full capabilities of the tools chosen.
- Practice continual improvement over the lifetime of each tool by dedicating resources to tuning and analytics and building custom use cases and content.
- Ensure that the tools chosen fit into a carefully designed monitoring, analysis, and response architecture.
8.1 Understanding the Constituency
Understand the organization we are going to protect.
What hosts are there?
The network between the hosts
What connections between IT assets and mission functions (business catalog)
Data to collect:
- Host name
- Media access control (MAC) address
- IP address
- OS and version
- Service pack and patch level
- Installed and running software
- Hardware details and configuration
- System settings
- Purchase date
- Personal owner, if applicable
- Organizational or project association, in some cases.
Network mapping
Vulnerability scanners are known to produce false positives and false negatives
8.2 Network Monitoring
Three things in order to perform competent network monitoring:
- An initial tip-off capability such as a signature- or behavior-based Intrusion detection systems (IDS). This includes the ability to leverage custom signatures and full details on the signature or behavior that fired (e.g., signature syntax).
- NetFlow records that show a summary of communications to and from the hosts listed in tip-off information, days or weeks before and after the tip-off fired
- The packet capture for the packet(s) that triggered the alert, preferably for the full session, in the form of libpcap-formatted data (PCAP).
If we wish to use multiple incompatible monitoring programs (e.g., both COTS and FOSS), they can be separated into different
VMs. These can run on top of typical virtualization technology such as VMware ESXi/ESX Server [155] or Xen [156]. While adding some complexity, this approach adds a great deal of flexibility not found in a bare-metal OS install, as described in the following:
- Collapsing multiple, disparate sensors onto one system with fewer wasted resources
- Modular addition, removal, and transition from one monitoring technology to another Remote reconstitution, provisioning, and upgrades of guest OSes and their entire monitoring software suite
- Mix of multiple, incompatible monitoring technologies on the same interface, such as a FOSS solution running in one VM and a COTS virtual appliance running in another
- From a software and management perspective, each monitoring tool appears on a separate virtual host. When collecting events centrally, this makes sorting and cor- relating alerts for the analyst less ambiguous.
Malware Detonation and Analysis
8.2.8 Honeypots
8.2.9 The Fate of the Network Intrusion Detection System
8.3 Host Monitoring and Defense
- AV/antispyware
- Intrusion detection and prevention
- Application blacklisting and whitelisting
- Configuration tracking
- Network access control
- Host-based firewall
- IP loss prevention
- User activity monitoring
- Remote incident and forensics support.
Host Intrusion Detection System/Host Intrusion Prevention System
Cause more problems because
First, they are deeply integrated with the host OS causing conflicts
Second, when deploying to large numbers of hosts (servers and desktops) can cause interuptions
8.4 Security Information and Event Management (SIEM)
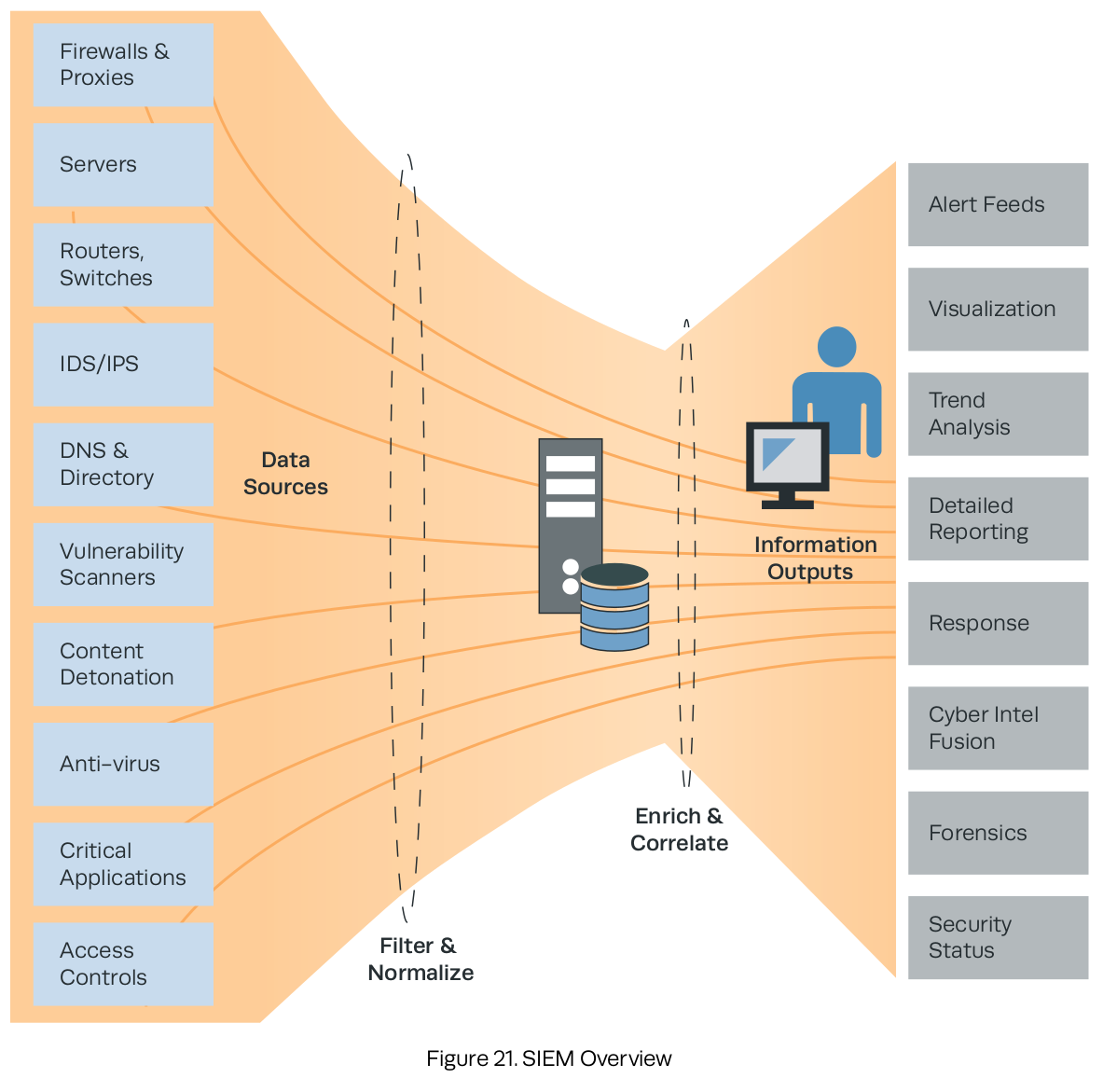
- Perimeter network monitoring. Classic monitoring of the constituency for malware and external threats
- Insider threat and audit. Data collection and correlation that allow for detection and monitoring for profiles of suspicious internal threat activity
- APT detection. Piecing together disparate data indicating lateral movement, remote access, command and control, and data exfiltration
- Configuration monitoring. Alerting on changes to the configuration of enterprise servers and systems, from password changes to critical Windows registry modifications
- Workflow and escalation. Tracking an event and incident from cradle to grave, including ticketing/case management, prioritization, and resolution
- Incident analysis and network forensics. Review and retention of historical log data Cyber intel fusion. Integration of tippers and signatures from cyber intel feeds
- Trending. For analysis of long-term patterns and changes in system or network behavior
- Cyber SA. Enterprise-wide understanding of threat posture
- Policy compliance. Built-in and customizable content that helps with compliance and reporting for laws such as the Federal Information Security Management Act.
